Understanding the TCP/IP Protocol

TCP/IP is the protocol underpinning the internet. But what is it and what does it do?
TCP/IP is actually two protocols, TCP and IP, that enable data to be transmitted over the internet. The IP protocol is responsible for transmitting data between two points, however it does not make any guarantees that transmission is done reliably. Data that is sent may get lost due to transmission errors along the way. TCP works together with IP and is designed to solve the problem of delivery reliability by ensuring that data does actually reach the intended destination.
Imagine two people who want to view web pages and have only a single broadband line between them to access the internet. One way the line could be shared is the first person uses it and then when they are finished with the web they allow the second person to use the line. If the first person subsequently wants to view more web pages, they have to wait until the line is free again.
Where a user obtains exclusive use of a phone line for a defined period of time before being passed to someone else is called circuit switching. This method of sharing a connection has two main problems. The person who does not currently have exclusive use of the line has to wait for the person who does to entirely finish with it before they can view a web page, which might be a very long time. The second problem is that the line is not used very efficiently.
A user viewing web pages is not necessarily communicating over the broadband line all of the time. They may download a web page, which takes a second or less, but then spend several minutes reading it. During the minutes the user spends reading the web page, the phone line is completely unused.
A more efficient approach is to interleave web page downloads for both users. While the first user is busy reading, the line may be used by the second user to download their web page. While the second user is reading, the line may be used by the first user to download their page and so on. Rapidly alternating access to the line between the users improves efficiency and increases utilisation of the phone line, that is it reduces the proportion of the time the expensive line sits idle. Now both users can receive their web pages quickly without having to wait for the other to finish with it first.
A problem though is what happens if one of the users downloads a large file, which may take many minutes? The phone line will then become blocked by the large download and the other user will not be able to access the web until the download completes.
In the following example user 1 requests a large file at time = 1, which will take 5 time units to complete. A second user requests a web page at time = 3, which will take one time unit to complete, but it cannot be delivered because the file download for user 1 is monopolising the line and so the web page is delayed. The file download completes at time = 5 and user 1 receives the file. Only now is the line free and the web page for user 2 can be downloaded, which is received at time = 6.
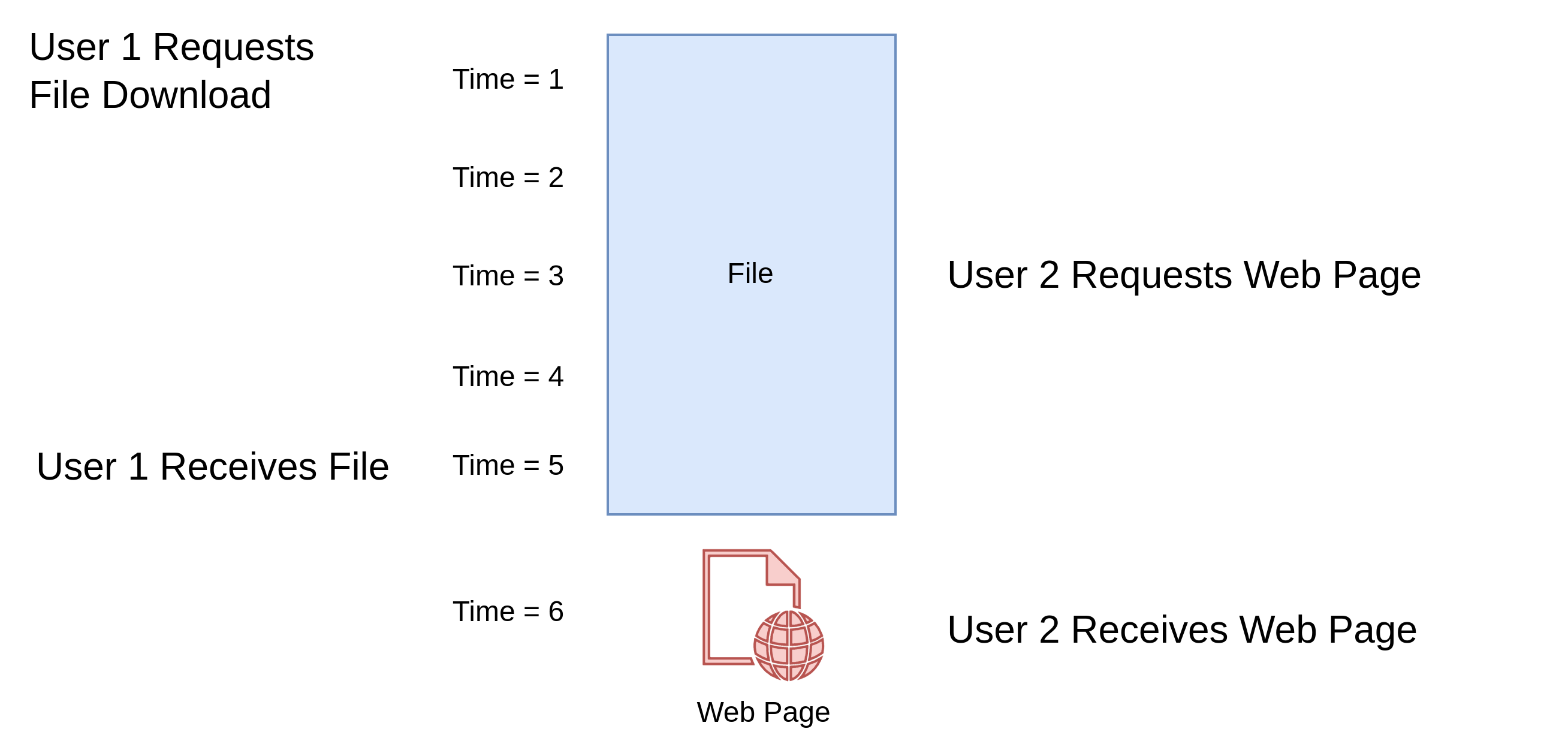
The large file download is not expected to be received instantly but browsing the web is a more interactive experience and the page should be delivered as quickly as possible. It is an inconvenience to the second user that there is a delay.
A solution to this problem is to split the large download into small chunks. A chunk of the file is sent, then it is checked if anyone else wants to use the line. If there are no other requests pending, then another chunk is sent. If however, the second user wants to retrieve a web page part way through the download, then that request is served and then the system gets back to sending more chunks of the large download for the first user. Now the second user doesn't have to wait for the download to complete to retrieve their web page.
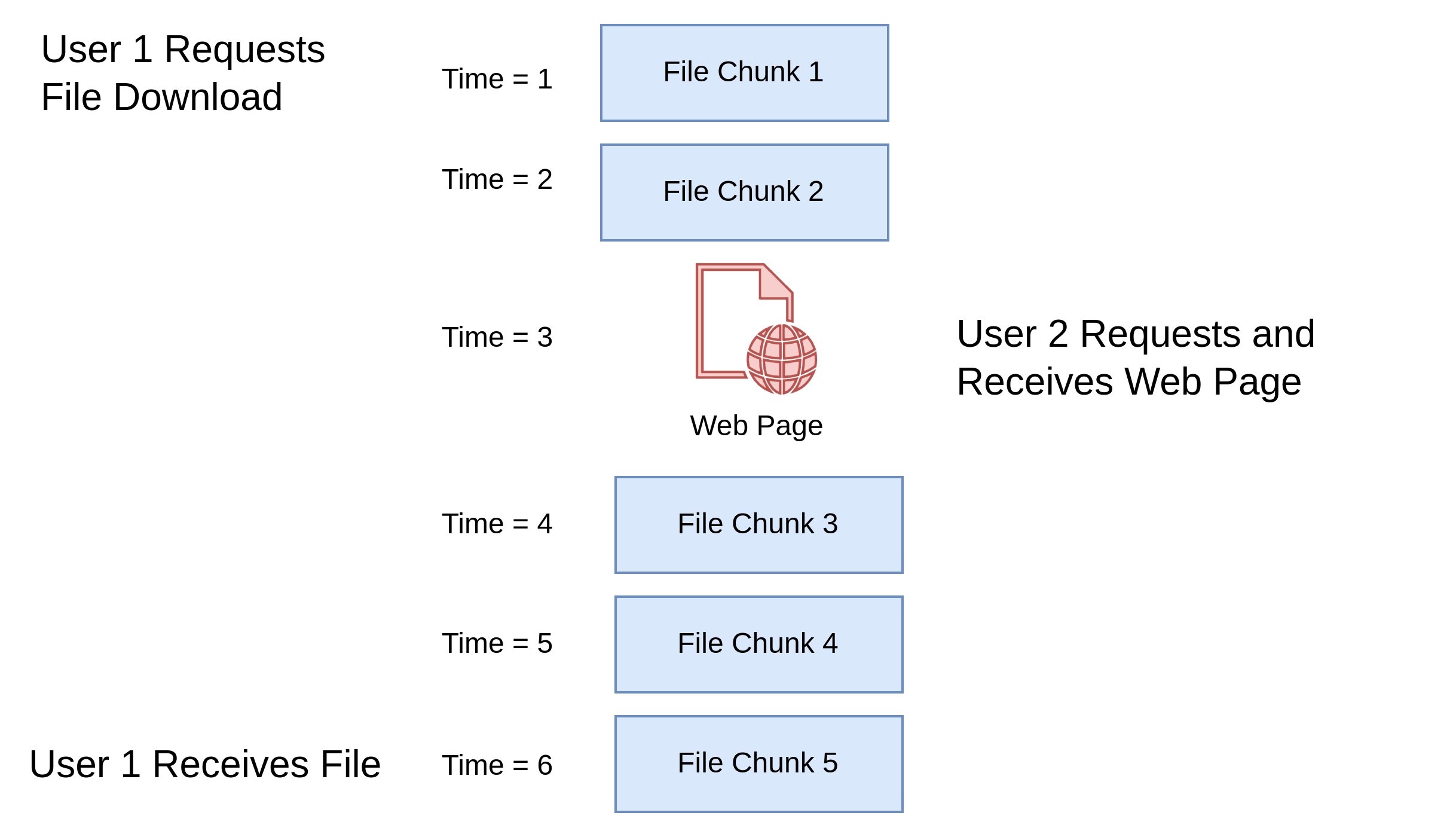
The IP protocol does exactly this to facilitate multiple users sharing a phone line simultaneously with the minimum of delay to each user. Each chunk of data is called a packet.
Another problem IP solves is how to get each packet (chunk of data) to the correct destination. When you send a letter, it is not usually driven directly from the post box to the destination but more usually passes through a number of hubs. For example, first the letter may be collected and delivered to a local sorting office in your town. At that office, the address is inspected and the letter is sent to a larger hub in a major city. From there it may pass to another major city somewhat nearer the destination town, then to the sorting office in the destination town and finally it will be delivered to the exact destination address.
The internet works in a similar way. The provider of your internet will most usually have no direct connection at all to the service you are trying to reach. Your packets of data will typically pass through a series of hubs to reach the destination. Each of the hubs will get the packet closer to the destination until the final hub knows how to to deliver it.
The process of deciding which series of hubs are needed to get to the destination is another problem the IP protocol helps with. Devices called routers make the decisions about where packets should be sent. Each IP packet has two addresses, a source address and a destination address. The router examines the destination address and from that decides where each packet needs to go. Routing data that has been split into chunks is packet switching.
There are two forms of internet addresses currently in use. The first kind is called IPv4 (meaning version 4 of the IP protocol) and the second kind is called IPv6 (IP version 6). An IPv4 address is a 32-bit number and is usually written as 4 x 8-bit numbers separated by a dot e.g. 192.168.0.1. As IPv4 addresses are a 32-bit number, there are 2^32 possible addresses, or about 4 billion. Every device on the internet needs an address and 4 billion was thought to be plenty in 1981 when the specification was published, however as internet use exploded in subsequent decades, it has turned out to be not enough. This was the main reason for the development of IPv6, which uses addresses that are 128-bit. The number of addresses that are possible with 128 bits is 3.4 x10^38, which is an exceptionally large number and really is probably enough addresses this time! Both types of address are in use simultaneously on the internet. Computers are given one type or the other or both. Where a computer has both kinds of addresses, either can be used to deliver a packet to the machine.
To help the router to know where to send the packet it is provided with a routing table. This is a list of ranges of IP addresses and corresponding destinations (usually another router). The router looks up which range in the table the packet destination address is within and sends it to corresponding next router mentioned in the table. The address ranges represent large portions of the internet. For example if a packet starts in the USA and the routing table matches against an address range known to be in the UK, then the routing table may instruct the device to send the packet down a line connected to a London router. The US based router has no idea how to get the packet to the final destination, but it knows from it's routing table that London is nearer to where the packet needs to be since it seems to be a UK address. The London based router might have more refined information that the packet destination is actually in Edinburgh and so it sends it on to another router located there. This router may have more refined information still about which exact customer telephone line has that address and is able to deliver the packet down the correct line.
You quite probably have a router in your home connected to your broadband. This router has a very simple routing table that makes a decision as to if any packet should stay within your home or be sent to the wider internet. If it decides the packet is destined for the internet, the routing table contains the address of another router at your internet provider.
We now have a method of getting packets to the destination but there is a problem of reliability. A router may send a packet to the next router, in the hope it is delivered, but has no method of confirming if it ever got there. Some distant router in a far off country may not be functioning or a phone line may be broken. How is the sender to know? IP splits data into packets, but the packets might arrive in entirely the wrong order. This would cause the file to reassembled from all the packets incorrectly. A router might duplicate a packet accidentally and the recipient gets two copies, or there might be errors on the transmission line and the packet content is corrupted. TCP is designed to help with these problems.
TCP is a special data format that is carried at the start of an IP packet and provides extra information. The TCP format is at least 20 bytes long, but optionally can be longer carrying additional information and is often drawn in the following style in groups of 4 bytes. Initially, we are only going to discuss the highlighted sections:
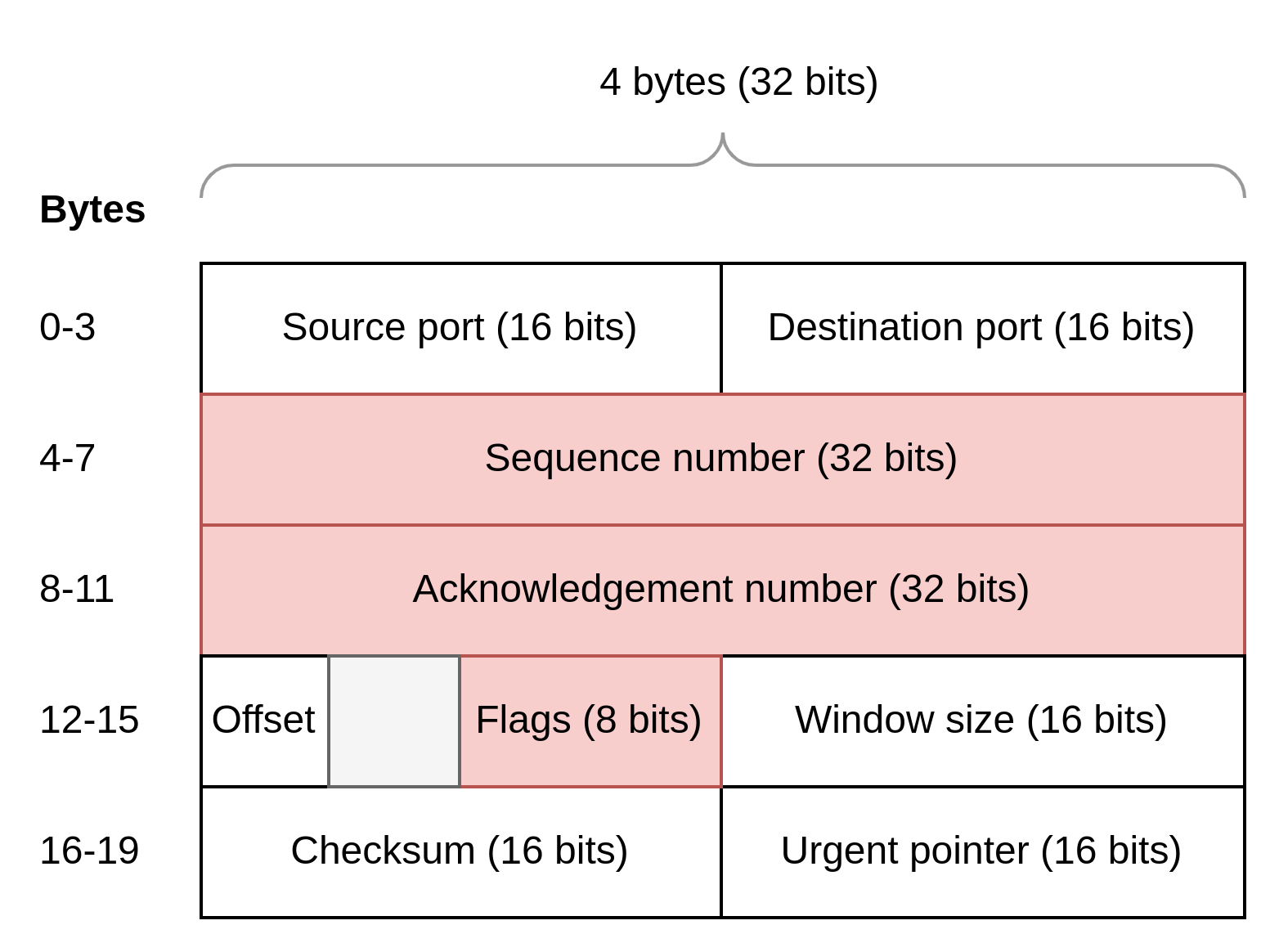
When a computer wants to communicate with another it sends a packet to it with a particular bit set to 1 called the SYN flag, which means synchronise. The SYN flag can be found in the highlighted "flags" section of the format diagram and is the 7th from the left of the 8 bits making up this section. If the destination computer receives the packet and agrees to communicate, it returns a packet to the sender with a flag called ACK set (for acknowledgement) in addition the SYN flag. The ACK flag is the 4th from the left of the 8 flag bits. The original sending computer now returns another packet with only the ACK flag set to 1. This process is called the three way handshake and establishes that the two parties wish to communicate.
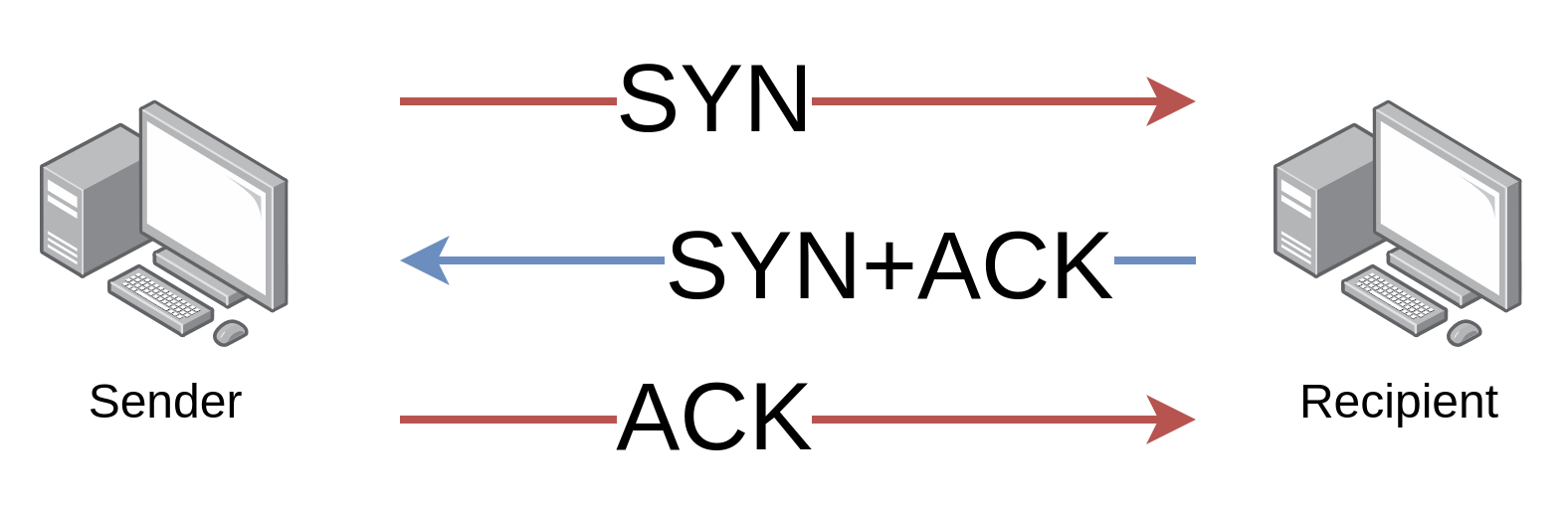
Now communication is established, the sending machine starts transmitting the data. For every packet it sends, it increases a sequence number in the packet. That is, it numbers each packet in sequential order. Using this numbering, the recipient can know if there is a packet missing, as there would be a gap in the sequence numbers. It can also know if a packet was received twice, as it will receive a repeat of the same sequence number, and it can determine the correct ordering of the data as all it has to do is sort the packets by the sequence numbers.
The recipient acknowledges each packet received by sending a packet back with the ACK bit set. It also sends a number called the acknowledgement number which is the size of data it has received. The sender then knows that the recipient received data of the intended length. The next sequence number used by the sender is the size of the previous packet. If the recipient spots some missing data, it can proactively let the sender know by sending back a packet with the ACK bit set and the sequence number it was expecting.
When the sender has completed sending the file, it sets a flag called FIN for finish and this is acknowledged by the other end. The recipient can also close the connection with a FIN if it does not wish to receive any more data.